Blog
Entanet FTTC Connection for DrayTek Vigor 2860/2862
You will need to configure the following pages:
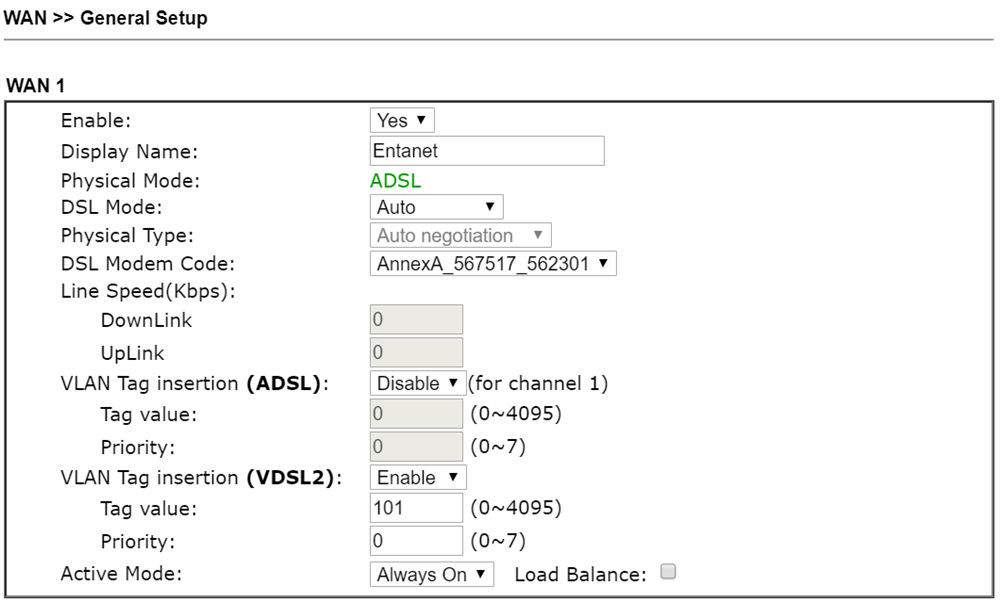
WAN>General Set-up
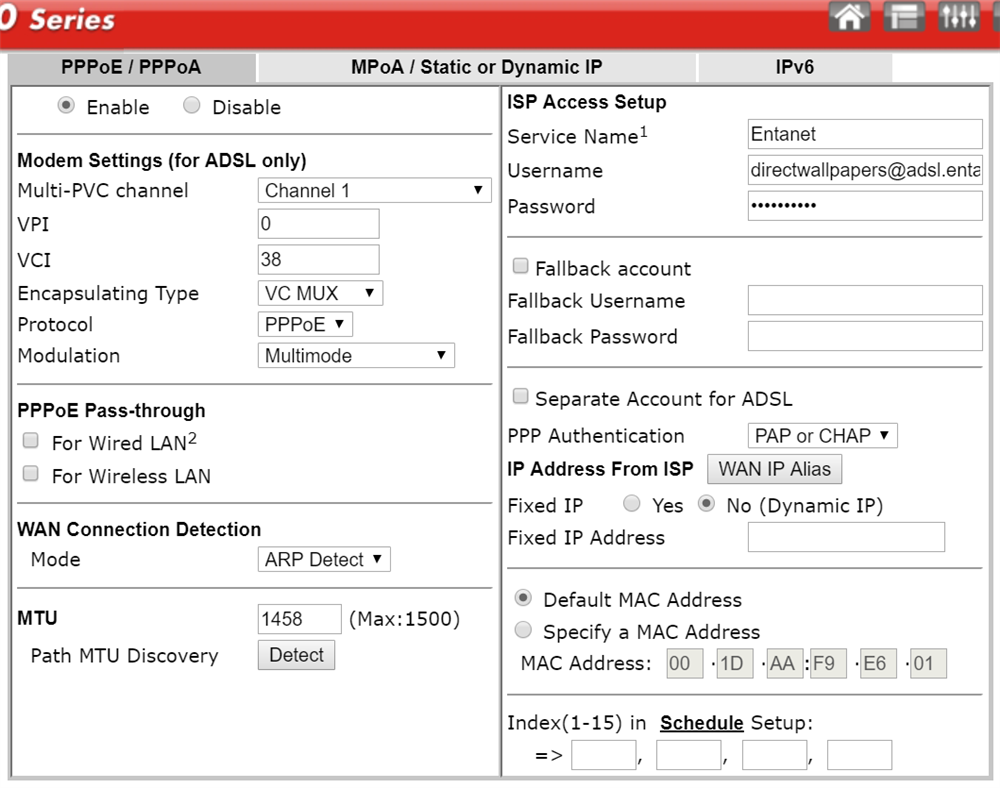
WAN>Internet Access
FTTC Details:
MTU: 1458
VPI=0
VC=38
Connection is: PPPoE
Encapsulation: VC MUX
VLAN TAG: 101
domain .com Final Notice - Spam Warning !!!
This one is worth mentioning just because they spray it out to every domain owner on the planet and occassionally it looks mildyly convincing, as in this case:
Servicese
From: Domain Service <[email protected]>
Sent: 08 January 2019 13:06
To: Domains Team
Subject: domain.com Final Notice
|
| Amount: | Term: | ||
domain.com | 01/28/2019 to 01/28/2020 | $86.00 | 1 Year |
Domain Name: domain.com |
This important expiration notification notifies you about the expiration notice of your domain registration for domain.com search engine optimization submission. The information in this expiration notification may contain legally privileged information from the notification processing department of the Domain Seo Service Registration to our search engine traffic generator. We do not register or renew domain names. We are selling traffic generator software tools. This information is intended for the use of the individual(s) named above. |
Failure to complete your seo domain name registration domain.com search engine optimization service process may make it difficult for customers to find you on the web. Process Payment for Secure Online Payment |
Act immediately
This domain seo registration for domain.com search engine service optimization notification will expire 01/14/2019.
Instructions and Unlike Instructions from this Newsletter:
You have received this message because you elected to receive notification. If you no longer wish to receive our notifications, please unlike here. If you have multiple accounts with us, you must opt out for each one individually to unlike receiving notifications. We are a search engine optimization company. We do not directly register or renew domain names. This is not a bill. You are dont need to pay the amount unless you accept this notification. This message, which contains promotional material strictly along the guidelines of the Can-Spam act of 2003. We have clearly mentioned the source mail-id of this email, also clearly mentioned our subject lines and they are in no way misleading. Please do not reply to this email, as we are not able to respond to messages sent to this address.
The 'secure' online payment link actually points to: http://pc1231.lopcholland.pw/em/link.php which is actually an alias of http://www.webcomdot.org which is an unsecured credit card fraud site.
Please report both of these domains as fraudulent and report the email originator as a spam source.
01785 463 178 BT Fake Calls - you are going to be disconnected, press 1
We have been receiving reports of suspect phone calls, allegedly from BT stating that the service is about to be shut down and to please press 1 for details.
Now we have not taken the plunge of actually pressing 1 to speak to someone but can report that the 1471 lookup gives a number of 01785463178 which will not receive calls 'the number you have called is not recognised' which seems odd as it is the BT service that gives the number in the first place and so it should be correct.
These calls are being received by people who are on the BT 152 call protect privacy service which seems strange as you would think that the numbers would be protected.
Either way none of the customers of BT being contacted have had their service removed and so this is obviously a scam.
If we intercept a call we will try speaking to someone to find out what they are trying to extract from people and report back.
Urgent to all residents of the building - Spam Warning !!
This email is interesting as it appears to be aimed at smaller companies sharing a large office building where staff may not know the name of the fire-safety officer or building administrator.
The email itself, however, is very simple and has no signature to impress authority on anyone:
From: Frances Moyer <[email protected]>
Sent: 11 December 2018 13:43
To: Support
Subject: Urgent to all residents of the building
Hi All,
Please find below the Up to date emergency exit map.
Thanks,
Frances Moyer,
Estate Management
PayPal Automatic Notification - Spam Warning!!
This email has been seen today in the UK:
From: PayPal Services <[email protected]>
Sent: 11 December 2018 18:47
To: Accounts Team
Subject: PayPal Automatic Notification
|
|
|
You got notification from DocuSign Electronic Service - Spam Warning!!
This email, posing as a Docusign email, is actually from qualitybumper.com.
The email itself attempts to persuade you to open a link to 'review an invoice' from DocuSign:
From: DocuSign Signature Service <[email protected]>
Sent: 10 December 2018 17:44
To: Accounts Team
Subject: You got notification from DocuSign Electronic Service
|
|
|
Your Name - Our meeting today at 8:00 PM ... - SPAM!!!
More from our fraudulent friends at 'Who's Dumb Enough to Think you can be a Bitcoin Millionaire'
This email is disingenuous from start to finish, as befits these people.
Of course there is no meeting and they have no idea of your name, they just extracted the text field from your email address, but let us have a look at the email and site anyway as these people do need to be publicly 'outed' or they will continue to prey on the weak and poor...
From: Arleen Weatherly <[email protected]>
Sent: 13 November 2018 16:15
To: Your Name
Subject: Your Name - Our meeting today at 8:00 PM ...
Hey,
I wanted to remind you of our today's meeting at 8:00 PM on this website:
http://r.meeting-online.ml/bL5j9gTqAx
At this meeting, I will explain in detail how you can effectively invest in the Bitcoin market and start
earning 1,293,186 pounds annually.
Yes, 1,293,186 pounds a year! Exactly that much I managed to earn in 2018by using this extremely
simple technique.
Watch the video and see how easy it is:
http://r.meeting-online.ml/bL5j9gTqAx
Register your free account and activate your trading account, and at 8:00 PM you will be able to
participate in our online meeting, where I will share my knowledge and investment techniques.
What is your dream? New home? A car? Or maybe a financial security?
Thanks to Bitcoin, tens of thousands of people have become millionaires. It is still possible - and I will
prove to you at the meeting tonigh!
Do not waste your time and register now:
http://r.meeting-online.ml/bL5j9gTqAx
Your personal Webinar access code:
0DQNBHZGMP4QRS
See you at the meeting!
Arleen Weatherly
Now we have no idea what the website meeting-online.ml is supposed to be but the owner is registered at:
Mali Dili B.V.
Point ML administrator
P.O. Box 11774
1001 GT Amsterdam
Which doesn't help much.
Either way the website doesn't seem to function at it's route - it just shows the apache hello message.
But at the link above, it shows our friends:

Now I don't know who that person is or how they got this way so young but that definitely looks like their parents house to me, I wouldn't buy that lamp now, never mind at that age.
As usual, if you try and leave you get a message saying:

This page is reproduced across many domain names such as:
https://en.bitcoinmillions.xyz/?a=6707&o=7613&s=181113mtuk
As you can see from the EN part, they reproduce their scam in most european languages...
In fact they have:
DNS name=de.bitcoinmillions.xyz
DNS name=en.bitcoinmillions.xyz
DNS name=es.bitcoinmillions.xyz
DNS name=it.bitcoinmillions.xyz
DNS name=nl.bitcoinmillions.xyz
DNS name=pl.bitcoinmillions.xyz
DNS name=se.bitcoinmillions.xyz
So please report this domain as fraudulent to as many government bodies as you can.
You're A Winner - The National Lottery - Winning Notification Letter 2018-dispatched Spam
Occassionally there is a spam email circulating that really makes you giggle, and here is a perfect example. Not only is this email sent to a generic email address - in this case a support@ address.
The message has only one piece of text and a PDF. The text reads:
'This message was sent to [email protected]. If you are not the owner of this email and you receive this message. Please discard the letter.'
The following email is very common at the moment:
From: [email protected]
Sent: 22 October 2018 16:05
To: Recipient
Subject: password (r9vrts4) for [email protected] is compromised
Hello!
I'm a hacker who cracked your email and device a few months ago.
You entered a password on one of the sites you visited, and I intercepted it.
This is your password from [email protected] on moment of hack: r9vrts4
Of course you can will change it, or already changed it.
But it doesn't matter, my malware updated it every time.
Do not try to contact me or find me, it is impossible, since I sent you an email from your account.
Through your email, I uploaded malicious code to your Operation System.
I saved all of your contacts with friends, colleagues, relatives and a complete history of visits to the
Internet resources.
Also I installed a Trojan on your device and long tome spying for you.
You are not my only victim, I usually lock computers and ask for a ransom.
But I was struck by the sites of intimate content that you often visit.
I am in shock of your fantasies! I've never seen anything like this!
So, when you had fun on piquant sites (you know what I mean!) I made screenshot with using my
program from your camera of yours device.
After that, I combined them to the content of the currently viewed site.
There will be laughter when I send these photos to your contacts!
BUT I'm sure you don't want it.
Therefore, I expect payment from you for my silence.
I think $883 is an acceptable price for it!
Pay with Bitcoin.
My BTC wallet: 1JTtwbvmM7ymByxPYCByVYCwasjH49J3Vj
If you do not know how to do this - enter into Google "how to transfer money to a bitcoin wallet". It is
not difficult.
After receiving the specified amount, all your data will be immediately destroyed automatically. My
virus will also remove itself from your operating system.
My Trojan have auto alert, after this email is read, I will be know it!
I give you 2 days (48 hours) to make a payment.
If this does not happen - all your contacts will get crazy shots from your dark secret life!
And so that you do not obstruct, your device will be blocked (also after 48 hours)
Do not be silly!
Police or friends won't help you for sure ...
p.s. I can give you advice for the future. Do not enter your passwords on unsafe sites.
I hope for your prudence.
Farewell.
This email is particularly annoying because it is not actually an email at att - just a telnet session being run against the email server pretending to be an email from your own mailbox. It is bypassing SPF and spoofing detection in some cases but it does not mean that any passwords have been hacked in any way or that they have compromised your computer in any way.
It is fairly obvious from the quality of the email that this is just an email sent out en masse in order to try and recover a few bit coin payments. The IP address can be found to show the originating IP in the email header and it is changing constantly perhaps suggesting that this is an email fired out by smtp viruses on various computers around the web.
The best action to take is to ensure that your own email address is not in yoru whitelist so that anti-spoofing and SPF measures block this email rather than letting it through.












